HackSys极度易受攻击的驱动程序
ooooo ooooo oooooooooooo oooooo oooo oooooooooo.
`888' `888' `888' `8 `888. .8' `888' `Y8b
888 888 888 `888. .8' 888 888
888ooooo888 888oooo8 `888. .8' 888 888
888 888 888 " `888.8' 888 888
888 888 888 o `888' 888 d88'
o888o o888o o888ooooood8 `8' o888bood8P'
HackSys极度易受攻击的驱动程序(HEVD)是一个故意设计为易受攻击的Windows内核驱动程序。它专为安全研究人员和爱好者开发,旨在提高他们在内核级漏洞利用方面的技能。
HEVD提供了一系列漏洞,从简单的栈缓冲区溢出到更复杂的问题,如释放后使用、池缓冲区溢出和竞争条件。这使研究人员能够探索每种已实现漏洞的利用技术。
2016年黑帽军火库
博客文章
外部漏洞利用
- https://github.com/sam-b/HackSysDriverExploits
- https://github.com/sizzop/HEVD-Exploits
- https://github.com/badd1e/bug-free-adventure
- https://github.com/FuzzySecurity/HackSysTeam-PSKernelPwn
- https://github.com/theevilbit/exploits/tree/master/HEVD
- https://github.com/GradiusX/HEVD-Python-Solutions
- http://pastebin.com/ALKdpDsF
- https://github.com/Cn33liz/HSEVD-StackOverflow
- https://github.com/Cn33liz/HSEVD-StackOverflowX64
- https://github.com/Cn33liz/HSEVD-StackCookieBypass
- https://github.com/Cn33liz/HSEVD-ArbitraryOverwrite
- https://github.com/Cn33liz/HSEVD-ArbitraryOverwriteGDI
- https://github.com/Cn33liz/HSEVD-StackOverflowGDI
- https://github.com/Cn33liz/HSEVD-ArbitraryOverwriteLowIL
- https://github.com/mgeeky/HEVD_Kernel_Exploit
- https://github.com/tekwizz123/HEVD-Exploit-Solutions
- https://github.com/FULLSHADE/Windows-Kernel-Exploitation-HEVD
- https://github.com/w4fz5uck5/3XPL01t5/tree/master/OSEE_Training
外部博客文章
- http://niiconsulting.com/checkmate/2016/01/windows-kernel-exploitation/
- http://samdb.xyz/2016/01/16/intro_to_kernel_exploitation_part_0.html
- http://samdb.xyz/2016/01/17/intro_to_kernel_exploitation_part_1.html
- http://samdb.xyz/2016/01/18/intro_to_kernel_exploitation_part_2.html
- http://samdb.xyz/2017/06/22/intro_to_kernel_exploitation_part_3.html
- https://sizzop.github.io/2016/07/05/kernel-hacking-with-hevd-part-1.html
- https://sizzop.github.io/2016/07/06/kernel-hacking-with-hevd-part-2.html
- https://sizzop.github.io/2016/07/07/kernel-hacking-with-hevd-part-3.html
- https://sizzop.github.io/2016/07/08/kernel-hacking-with-hevd-part-4.html
- https://www.fuzzysecurity.com/tutorials/expDev/14.html
- https://www.fuzzysecurity.com/tutorials/expDev/15.html
- https://www.fuzzysecurity.com/tutorials/expDev/16.html
- https://www.fuzzysecurity.com/tutorials/expDev/17.html
- https://www.fuzzysecurity.com/tutorials/expDev/18.html
- https://www.fuzzysecurity.com/tutorials/expDev/19.html
- https://www.fuzzysecurity.com/tutorials/expDev/20.html
- http://dokydoky.tistory.com/445
- https://hshrzd.wordpress.com/2017/05/28/starting-with-windows-kernel-exploitation-part-1-setting-up-the-lab/
- https://hshrzd.wordpress.com/2017/06/05/starting-with-windows-kernel-exploitation-part-2/
- https://hshrzd.wordpress.com/2017/06/22/starting-with-windows-kernel-exploitation-part-3-stealing-the-access-token/
- https://osandamalith.com/2017/04/05/windows-kernel-exploitation-stack-overflow/
- https://osandamalith.com/2017/06/14/windows-kernel-exploitation-arbitrary-overwrite/
- https://osandamalith.com/2017/06/22/windows-kernel-exploitation-null-pointer-dereference/
- http://dali-mrabet1.rhcloud.com/windows-kernel-exploitation-arbitrary-memory-overwrite-hevd-challenges/
- https://blahcat.github.io/2017/08/31/arbitrary-write-primitive-in-windows-kernel-hevd/
- https://klue.github.io/blog/2017/09/hevd_stack_gs/
- https://glennmcgui.re/introduction-to-windows-kernel-exploitation-pt-1/
- https://glennmcgui.re/introduction-to-windows-kernel-driver-exploitation-pt-2/
- https://kristal-g.github.io/2021/02/07/HEVD_StackOverflowGS_Windows_10_RS5_x64.html
- https://kristal-g.github.io/2021/02/20/HEVD_Type_Confusion_Windows_10_RS5_x64.html
- https://wafzsucks.medium.com/hacksys-extreme-vulnerable-driver-arbitrary-write-null-new-solution-7d45bfe6d116
- https://wafzsucks.medium.com/how-a-simple-k-typeconfusion-took-me-3-months-long-to-create-a-exploit-f643c94d445f
- https://mdanilor.github.io/posts/hevd-0/
- https://mdanilor.github.io/posts/hevd-1/
- https://mdanilor.github.io/posts/hevd-2/
- https://mdanilor.github.io/posts/hevd-3/
- https://mdanilor.github.io/posts/hevd-4/
作者
Ashfaq Ansari
ashfaq[at]hacksys[dot]io
截图
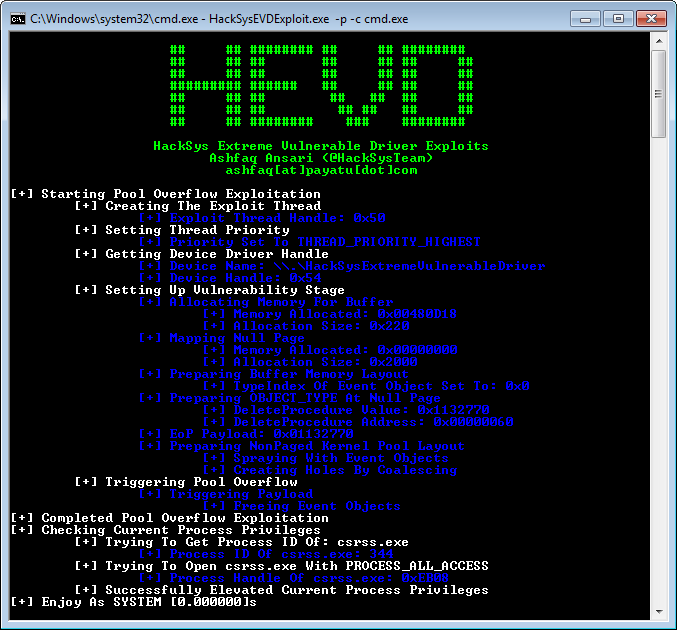
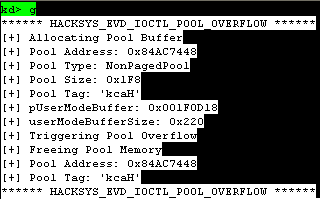
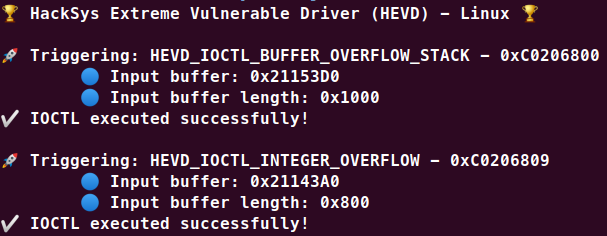
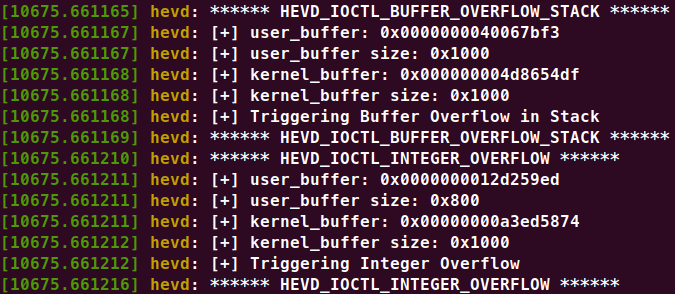
实现的漏洞
- 写入NULL
- 双重获取
- 缓冲区溢出
- 栈
- 栈GS
- 非分页池
- 非分页池Nx
- 分页池会话
- 释放后使用
- 非分页池
- 非分页池Nx
- 类型混淆
- 整数溢出
- 算术溢出
- 内存泄露
- 非分页池
- 非分页池Nx
- 任意递增
- 任意覆写
- 空指针解引用
- 未初始化内存
- 栈
- 非分页池
- 不安全的内核资源访问
构建驱动程序
- 安装Visual Studio 2017
- 安装Windows驱动程序工具包
- 运行适当的驱动程序构建器
Build_HEVD_Vulnerable_x86.bat或Build_HEVD_Vulnerable_x64.bat
下载
如果你不想从源代码构建HackSys极度易受攻击的驱动程序,你可以下载最新版本的预构建可执行文件:
https://github.com/hacksysteam/HackSysExtremeVulnerableDriver/releases
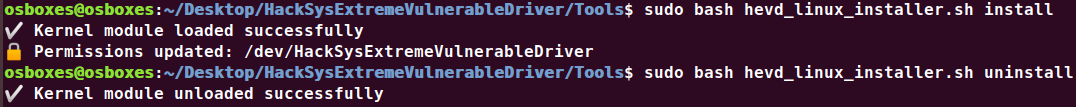
安装驱动程序
使用OSR驱动程序加载器来安装HackSys极度易受攻击的驱动程序
测试
HackSys极度易受攻击的驱动程序及其相应的漏洞利用已在Windows 7 SP1 x86和Windows 10 x64上进行了测试
已举办的培训课程
已举办的工作坊
Linux版HEVD
许可证
请查看LICENSE文件了解复制许可
贡献指南
请查看CONTRIBUTING.md文件了解贡献指南
待办事项和错误报告
请通过以下地址的GitHub问题跟踪器提交任何增强请求或错误报告:https://github.com/hacksysteam/HackSysExtremeVulnerableDriver/issues
致谢
感谢这些wonderful的人:🎉

 访问官网
访问官网 Github
Github 论文
论文














